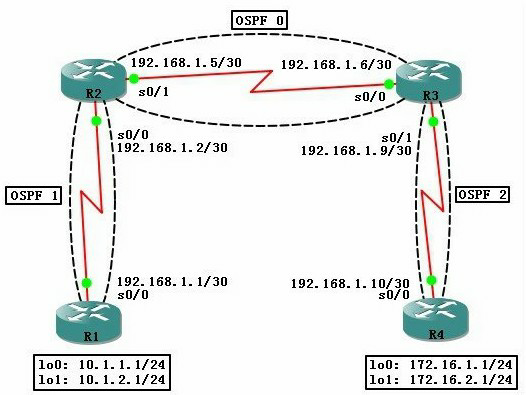
网络图:
配置各路由器的IP地址信息,OSPF信息,并测试连通性。
查看R1和R2的OSPF路由表:
R1>show ip route OSPF
O IA 172.16.0.0/16 [110/193] via 192.168.1.2, 00:15:14, Serial0/0
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:15:14, Serial0/0
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:15:21, Serial0/0
R2>show ip route ospf
O IA 172.16.0.0/16 [110/129] via 192.168.1.6, 00:17:01, Serial0/1
10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
O 10.1.2.1/32 [110/65] via 192.168.1.1, 00:17:01, Serial0/0
O 10.1.1.1/32 [110/65] via 192.168.1.1, 00:17:01, Serial0/0
O 10.1.0.0/16 is a summary, 00:17:01, Null0
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/128] via 192.168.1.6, 00:17:01, Serial0/1
在R1上启用明文认证:
R1(config)#int s0/0
R1(config-if)#ip ospf authentication
R1(config-if)#ip ospf authentication-key xiaoyang
R1(config-if)#exit
打开debug,查看系统提示:
*Mar 1 00:21:30.371: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial0/0 from FULL to DOWN, Neighbor Down: Dead timer expired
R1#debug ip ospf events
OSPF events debugging is on
R1#
*Mar 1 00:23:20.071: OSPF: Send hello to 224.0.0.5 area 1 on Serial0/0 from 192.168.1.1
*Mar 1 00:23:20.395: OSPF: Rcv pkt from 192.168.1.2, Serial0/0 : Mismatch Authentication type. Input packet specified type 0, we use type 1
在R2上启用明文认证:
R2(config)#int s0/0
R2(config-if)#ip ospf authentication
R2(config-if)#ip ospf authentication-key xiaoyang
R2(config-if)#exit
再观察R1上的调试信息:
*Mar 1 00:33:40.183: OSPF: Send hello to 224.0.0.5 area 1 on Serial0/0 from 192.168.1.1
*Mar 1 00:33:40.427: OSPF: Rcv pkt from 192.168.1.2, Serial0/0 : Mismatch Authentication Key - Clear Text
R1#
*Mar 1 00:33:50.187: OSPF: Send hello to 224.0.0.5 area 1 on Serial0/0 from 192.168.1.1
*Mar 1 00:33:50.455: OSPF: Rcv hello from 192.168.1.5 area 1 from Serial0/0 192.168.1.2
*Mar 1 00:33:50.459: OSPF: 2 Way Communication to 192.168.1.5 on Serial0/0, state 2WAY
*Mar 1 00:33:50.463: OSPF: Send DBD to 192.168.1.5 on Serial0/0 seq 0x142 opt 0x52 flag 0x7 len 32
*Mar 1 00:33:50.467: OSPF: End of hello processing
*Mar 1 00:33:50.507: OSPF: Rcv DBD from 192.168.1.5 on Serial0/0 seq 0xEDE opt 0x52 flag 0x7 len 32 mtu 1500 state EXSTART(启动状态)
*Mar 1 00:33:50.511: OSPF: NBR Negotiation Done. We are the SLAVE(从属的)
*Mar 1 00:33:50.511: OSPF: Send DBD to 192.168.1.5 on Serial0/0 seq 0xEDE opt 0x52 flag 0x2 len 132
*Mar 1 00:33:50.519: OSPF: Rcv DBD from 192.168.1.5 on Serial0/0 seq 0xEDF opt 0x52 flag 0x3 len 132 mtu 1500 state EXCHANGE(交换)
*Mar 1 00:33:50.523: OSPF: Send DBD to 192.168.1.5 on Serial0/0 seq 0xEDF opt 0x52 flag 0x0 len 32
*Mar 1 00:33:50.527: OSPF: Database request to 192.168.1.5
*Mar 1 00:33:50.527: OSPF: sent LS REQ packet to 192.168.1.2, length 12
*Mar 1 00:33:50.547: OSPF: Rcv DBD from 192.168.1.5 on Serial0/0 seq 0xEE0 opt 0x52 flag 0x1 len 32 mtu 1500 state EXCHANGE
*Mar 1 00:33:50.547: OSPF: Exchange Done with 192.168.1.5 on Serial0/0
*Mar 1 00:33:50.547: OSPF: Send DBD to 192.168.1.5 on Serial0/0 seq 0xEE0 opt 0x52 flag 0x0 len 32
*Mar 1 00:33:50.551: OSPF: Synchronized with 192.168.1.5 on Serial0/0, state FULL
*Mar 1 00:33:50.551: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial0/0 from LOADING to FULL, Loading Done
*Mar 1 00:34:00.191: OSPF: Send hello to 224.0.0.5 area 1 on Serial0/0 from 192.168.1.1
*Mar 1 00:34:00.427: OSPF: Rcv hello from 192.168.1.5 area 1 from Serial0/0 192.168.1.2
*Mar 1 00:34:00.431: OSPF: End of hello processing
清除所有认证信息,继续。
在R1上配置基于MD5的密码接口认证:
R1(config)#int s0/0
R1(config-if)#ip ospf aut
R1(config-if)#ip ospf authentication message-digest
R1(config-if)#ip ospf message-digest-key 1 md5 xiaoyang
R1(config-if)#exit
查看R1路由表:
R1(config)#do show ip route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback1
C 10.1.1.0 is directly connected, Loopback0
192.168.1.0/30 is subnetted, 1 subnets
C 192.168.1.0 is directly connected, Serial0/0
没有从OSPF学习到的路由信息。
在R2上配置基于MD5的密码接口认证:
R2(config)#int s0/0
R2(config-if)#no ip ospf au
R2(config-if)#no ip ospf authentication-k
R2(config-if)#ip ospf au me
R2(config-if)#ip ospf au message-digest
R2(config-if)#ip ospf message-digest-key 1 md5 xiaoyang
R2(config-if)#exit
观察R1上的系统反馈信息,并查看路由表:
R1(config)#
*Mar 1 00:56:20.559: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial0/0 from LOADING to FULL, Loading Done
R1(config)#do show ip route
Gateway of last resort is not set
O IA 172.16.0.0/16 [110/193] via 192.168.1.2, 00:00:26, Serial0/0
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback1
C 10.1.1.0 is directly connected, Loopback0
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:00:26, Serial0/0
C 192.168.1.0 is directly connected, Serial0/0
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:00:26, Serial0/0
R1和R2重新建立了邻居关系,并重新学习到了OSPF路由信息。
清除所有认证信息,继续。
在R1上启用区域的明文认证:
R1(config)#router ospf 1
R1(config-router)#area 1 authentication (为区域1启用OSPF的认证)
R1(config-router)#exit
R1(config)#int s0/0
R1(config-if)#ip ospf authentication-key xiaoyang(明文的)
R1(config-if)#exit
然后就可以看到那个啥又死了:
*Mar 1 00:03:39.603: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial0/0 from FULL to DOWN, Neighbor Down: Dead timer expired
查看R1的路由表:
R1#show ip route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback1
C 10.1.1.0 is directly connected, Loopback0
192.168.1.0/30 is subnetted, 1 subnets
C 192.168.1.0 is directly connected, Serial0/0
之前学习到的OSPF路由条目又没了。
再去R2上搞搞:
R2(config)#router ospf 1
R2(config-router)#area 1 authentication
R2(config-router)#exit
R2(config)#int s0/0
R2(config-if)#ip ospf authentication-key xiaoyang
R2(config-if)#exit
再去R1上看,又活过来了:
R1#
*Mar 1 00:10:01.143: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial0/0 from LOADING to FULL, Loading Done
R1#show ip route
Gateway of last resort is not set
O IA 172.16.0.0/16 [110/193] via 192.168.1.2, 00:00:31, Serial0/0
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback1
C 10.1.1.0 is directly connected, Loopback0
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:00:31, Serial0/0
C 192.168.1.0 is directly connected, Serial0/0
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:00:31, Serial0/0
清除所有认证信息,继续。
在R1和R2上配置基于MD5的密码区域认证:
R1(config-router)#area 1 authentication message-digest
R1(config-router)#exit
R1(config)#int s0/0
R1(config-if)#ip ospf message-digest-key 1 md5 xiaoyang
R1(config-if)#exit
*Mar 1 00:02:10.059: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial0/0 from FULL to DOWN, Neighbor Down: Dead timer expired
R2(config)#router ospf 1
R2(config-router)#area 1 authentication message-digest
R2(config-router)#exit
R2(config)#int s0/0
R2(config-if)#ip ospf message-digest-key 1 md5 xiaoyang
R2(config-if)#exit
R2(config)#
*Mar 1 00:04:31.379: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.2.1 on Serial0/0 from LOADING to FULL, Loading Done
正确配置后一切正常。
清除所有认证信息,继续。
配置更改md5密码,此配置主要用于弃用旧密码,启用新密码时可能会使用(同样适用于区域的md5认证):
R1(config)#int s0/0
R1(config-if)#ip ospf authentication message-digest
R1(config-if)#ip ospf message-digest-key 1 md5 xiaoyang1
R1(config-if)#ip ospf message-digest-key 2 md5 xiaoyang2
R1(config-if)#exit
当在接口出现两条md5的密码配置命令时,R2路由会发送两份不同的分组数据包。分别使用1和2的密码。
一旦新的密码2可以使用了,原的密码1就可以使用no命令取消。完成旧密码到新密码的迁移。